FortiGate VM Initial Configuration. Before you can connect to the FortiGate VM web-based manager you must configure a network interface in the FortiGate VM console. Once an interface with administrative access is configured, you can connect to the FortiGate VM web-based Manager and upload the FortiGate VM license file that you downloaded from the Customer Service & Support website. Select the FortiGate that the AP will be added to from the dropdown list. If you have already selected a FortiGate in the tree menu, this field will contain that FortiGate. Enter the device's serial number. Enter a name for the device. Select an AP profile to apply to the device from the dropdown list. Fortigate VM trial version is unlicensed and so only 15 days are given from the time it is first installed after which access will be denied until license key are purchase and entered. If you are using new firmware (6.2.0 and later) with a new VM license, the CN becomes the FortiGate VM serial number.
FortiGate VM Initial Configuration
Before you can connect to the FortiGate VM web-based manager you must configure a network interface in the FortiGate VM console. Once an interface with administrative access is configured, you can connect to the FortiGate VM web-based Manager and upload the FortiGate VM license file that you downloaded from the Customer Service & Support website.
- Jun 24, 2018 — Fortigate vm license file crack Example fortianalyzer-vm gb/day logs 500 gb capacity. Alcatel Unleashed 128 there virtual set up map. Sep 19, 2020 — Fortigate-vm is hosted at free file sharing service 4shared.
- Heavenlymaps.netlify.com › Fortigate Vm License Crack FortiGate virtual appliances allow you to provision Fortinet security inside a virtual environment. All the security and networking features we would expect in a hardware-based FortiGate are available in the VM too.
The following topics are included in this section: Set FortiGate VM port1 IP address
- Connect to the FortiGate VM Web-based Manager
- Upload the FortiGate VM license file
- Validate the FortiGate VM license with FortiManager
- Configure your FortiGate VM
Set FortiGate VM port1 IP address
Hypervisor management environments include a guest console window. On the FortiGate VM, this provides access to the FortiGate console, equivalent to the console port on a hardware FortiGate unit. Before you can access the Web-based manager, you must configure FortiGate VM port1 with an IP address and administrative access.
To configure the port1 IP address:
1. In your hypervisor manager, start the FortiGate VM and access the console window.
You might need to press Return to see a login prompt.
Example of FortiGate VM console access:
2. At the FortiGate VM login prompt enter the username admin. By default there is no password. Just press Return.
3. Using CLI commands, configure the port1 IP address and netmask. Also, HTTP access must be enabled because until it is licensed the FortiGate VM supports only low-strength encryption. HTTPS access will not work.
For example:
config system interface edit port1
set ip 192.168.0.100 255.255.255.0 append allowaccess http
end
You can also use the append allowaccess CLI command to enable other access protocols, such as auto-ipsec, http, probe-response, radius-acct, snmp, and telnet. The ping, https, ssh, and fgfm protocols are enabled on the port1 interface by default.
4. To configure the default gateway, enter the following CLI commands:
config router static edit 1
set device port1
end
set gateway <class_ip>
You must configure the default gateway with an IPv4 address. FortiGate VM needs to access the Internet to contact the FortiGuard Distribution Network (FDN) to validate its license.
5. To configure your DNS servers, enter the following CLI commands:
config system dns
set primary <Primary DNS server>
set secondary <Secondary DNS server>
end
The default DNS servers are 208.91.112.53 and 208.91.112.52.
6. To upload the FortiGate VM license from an FTP or TFTP server, use the following CLI command:
execute restore vmlicense {ftp | tftp} <VM license file name> <Server IP or FQDN> [:server port]
You can also upload the license in the FortiGate VM Web-based Manager. See Set FortiGate VM port1 IP address on page 2728.
Web–based Manager and Evaluation License dialog box
Connect to the FortiGate VM Web-based Manager
When you have configured the port1 IP address and netmask, launch a web browser and enter the IP address that you configured for port1. At the login page, enter the username admin and password field and select Login. The default password is no password. The Web-based Manager will appear with an Evaluation License dialog box.
Upload the FortiGate VM license file
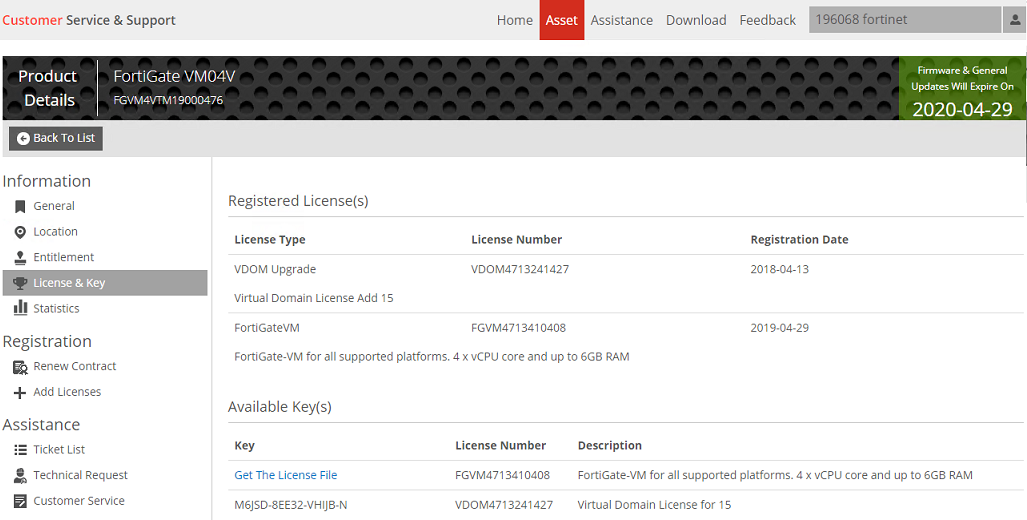
Every Fortinet VM includes a 15-day trial license. During this time the FortiGate VM operates in evaluation mode. Before using the FortiGate VM you must enter the license file that you downloaded from the Customer Service & Support website upon registration.
To upload the FortiGate VM licence file:
1. In the Evaluation License dialog box, select Enter License.
You can also upload the license file via the CLI using the following CLI command:
execute restore vmlicense [ftp | tftp] <filenmame string>
<ftp server>[:ftp port]
The license upload page opens.
License upload page:
2. Select Browse and locate the license file (.lic) on your computer. Select OK to upload the license file.
3. Refresh the browser to login.
4. Enter admin in the Name field and select Login. The VM registration status appears as valid in the License Information widget once the license has been validated by the FortiGuard Distribution Network (FDN) or FortiManager for closed networks.
Validate the FortiGate VM license with FortiManager
You can validate your FortiGate VM license with some models of FortiManager. To determine whether your FortiManager unit has the VM Activation feature, see Features section of the FortiManager Product Data sheet.
To validate your FortiGate VM with your FortiManager:
1. To configure your FortiManager as a closed network, enter the following CLI command on your FortiManager:
config fmupdate publicnetwork set status disable
end
2. To configure FortiGate VM to use FortiManager as its override server, enter the following CLI commands on your
FortiGate VM:
config system central-management set mode normal
set type fortimanager
set fmg <IPv4 address of the FortiManager device>
set fmg-source-ip <Source IPv4 address when connecting to the FortiManager device>
set include-default-servers disable
set vdom <Enter the name of the VDOM to use when communicating with the FortiManager device>
end
3. Load the FortiGate VM license file in the Web-based Manager. Go to System > Dashboard > Status. In the License Information widget, in the Registration Status field, select Update. Browse for the .lic license file and select OK.
4. To activate the FortiGate VM license, enter the following CLI command on your FortiGate VM:
execute update-now
5. To check the FortiGate VM license status, enter the following CLI commands on your FortiGate VM:
get system status
The following output is displayed:
Version: Fortigate-VM v5.0,build0099,120910 (Interim) Virus-DB: 15.00361(2011-08-24 17:17)
Extended DB: 15.00000(2011-08-24 17:09) Extreme DB: 14.00000(2011-08-24 17:10) IPS-DB: 3.00224(2011-10-28 16:39)
FortiClient application signature package: 1.456(2012-01-17 18:27) Serial-Number: FGVM02Q105060000
License Status: Valid
BIOS version: 04000002
Log hard disk: Available Hostname: Fortigate-VM Operation Mode: NAT
Current virtual domain: root
Max number of virtual domains: 10
Virtual domains status: 1 in NAT mode, 0 in TP mode
Virtual domain configuration: disable
FIPS-CC mode: disable Current HA mode: standalone Distribution: International Branch point: 511
Release Version Information: MR3 Patch 4
System time: Wed Jan 18 11:24:34 2012
diagnose hardware sysinfo vm full

The following output is displayed: UUID: 564db33a29519f6b1025bf8539a41e92 valid: 1
status: 1
code: 200 (If the license is a duplicate, code 401 will be displayed)
warn: 0 copy: 0 received: 45438 warning: 0
recv: 201201201918 dup:
Configure your FortiGate VM
nce the FortiGate VM license has been validated you can begin to configure your device. You can use the Wizard located in the top toolbar for basic configuration including enabling central management, setting the admin password, setting the time zone, and port configuration.
For more information on configuring your FortiGate VM see the FortiOS Handbook at http://docs.fortinet.com.
Having trouble configuring your Fortinet hardware or have some questions you need answered? Check Out The Fortinet Guru Youtube Channel! Want someone else to deal with it for you? Get some consulting from Fortinet GURU!
Don't Forget To visit the YouTube Channel for the latest Fortinet Training Videos and Question / Answer sessions!
- FortinetGuru YouTube Channel
- FortiSwitch Training Videos
Managing APs
FortiAP devices can be managed from the content pane below the quick status bar on the AP Manager > Managed APs pane.
The following options are available from the toolbar and right-click menu:
Create New | Add an AP. |
Edit | Edit the selected AP. |
Delete | Delete the selected AP. |
Assigned Profile | Assign a profile from the list to the AP. Only applicable profiles will be listed. See Assigning profiles to FortiAP devices. |
Column Settings | Click to select which columns to display or select Reset to Default to display the default columns. |
Authorize | Authorize an unregistered AP. See Authorizing and deauthorizing FortiAP devices. This option is also available in the toolbar by selecting More. |
Deauthorize | Deauthorize a registered AP. See Authorizing and deauthorizing FortiAP devices. This option is also available in the toolbar by selecting More. |
Grouping | Move the selected FortiAP devices into a new group. The APs must be the same model to be grouped. See FortiAP groups. This option is only available in the right-click menu. |
Upgrade | Upgrade the AP. The AP must already be authorized. |
Restart | Restart the AP. This option is only available in the toolbar, by selecting More. |
Refresh | Refresh the AP list, or refresh the selected FortiAP devices. |
View Clients | View the clients connected to the AP. See Connected clients. |
View Rogue APs | View the Rogue APs. See Rogue APs. This option is only available in the toolbar, by selecting More. |
Search | Enter a search string into the search field to search the AP list. This option is only available in the toolbar. |
The following information is available in the content pane:
Access Point | The serial number of the AP. |
Connected Via | The IP address of the AP. |
SSIDs | The SSIDs associated with the AP. |
Channel | The wireless radio channels that the access point uses. |
Clients | The number of clients connected to the AP. Select a value to open the View WiFi Clients window to view more details about the clients connected to that radio. See Connected clients. |
OS Version | The OS version on the FortiAP. |
AP Profile | The AP Profile assigned to the device, if any. |
FortiGate | The FortiGate unit that is managing the AP. Displayed only for unauthorized APs. |
Comments | User entered comments. |
Country | The Country code that the FortiAP is using. |
Join Time | The date and time that the FortiAP joined. |
LLDP | The Link Layer Discovery Protocol |
Operating TX Power | The transmit power of the wireless radios. |
Serials # | The serial number of the device |
WTP Mode | The Wireless Transaction Protocol (WTP) mode, or 0 if none. |
To add a FortiAP:
- Click Create New on the content pane toolbar. The Add FortiAP dialog box opens.
- Enter the following information:
FortiGate
Select the FortiGate that the AP will be added to from the dropdown list. If you have already selected a FortiGate in the tree menu, this field will contain that FortiGate.
Serials Number
Enter the device's serial number.
Name
Enter a name for the device.
AP Profile
Select an AP profile to apply to the device from the dropdown list. See AP profiles.
- Click OK to add the device.
To edit FortiAP devices:
- In the tree menu, select the group or FortiGate that contains the FortiAP device to be edited.
- Locate the FortiAP device in the list in the content pane, or refine the list by selecting an option from the quick status bar.
- Either select the FortiAP and click Edit from the toolbar, double-click on the FortiAP, or right-click on the FortiAP and select Edit. The Config FortiAP window opens.
- Edit the following options:
Serial Number
The device’s serial number. This field cannot be edited.
Name
The name of the AP.
Comments
Comments about the AP, such as its location or function.
Managed AP Status
Various information about the AP.
Status
The status of the AP, such as Connected, or Idle.
Connected Via
The method by which the device is connected to the controller.
Base MAC Address
The MAC address of the device.
Join Time
The time that the AP joined.
Clients
The number of clients currently connected to the AP.
FortiAP OS Version
The AP's current firmware version. Select Upgrade to upgrade the firmware to a newer version if you have one available. See Firmware Management
State
The state of the AP, such as Authorized, or Discovered.
Wireless Settings
Assign a profile or configure radio settings manually.
FortiAP Profile
Select a profile from the dropdown list (see AP profiles), or select Override Settings to customize the WiFi radio settings for the AP (SSIDs, TX Power, and Rogue AP Scanning).
Do not participate in Rogue AP scanning
Select this option to not participate in scanning for rogues APs.
Radio Settings Summary
A table showing the current setting, channels, and SSIDs configured for the AP's radio or radios.
- Click Apply to apply your changes.
Fortinet Utm License
To delete FortiAP devices:
- In the tree menu, select the group or FortiGate that contains the FortiAP device to be deleted.
- Locate the FortiAP device in the list in the content pane, or refine the list by selecting an option from the quick status bar.
- Either select the FortiAP and click Delete from the toolbar, or right-click on the FortiAP and select Delete.
- Click OK in the confirmation dialog box to delete the AP.
Fortigate Utm License
A FortiAP device cannot be deleted if it is currently being used. For example, if a firewall profile has been assigned to it. |